The humble telephone that Alexander Graham Bell once predicted would be in every town has gone through countless evolutions, especially since the dawn of the digital age. Unfortunately, one of the less desirable developments is the creation of vishing, a relatively new form of cybercrime that first appeared about 30 years ago, but has since become an increasingly popular — and concerning — cyberattack.
Vishing is used for both long-term and short-term scams, including identity theft, fraud, and others. Learn more about the history of vishing scams, their current threat level, and how to recognize and prevent yourself from being victimized.
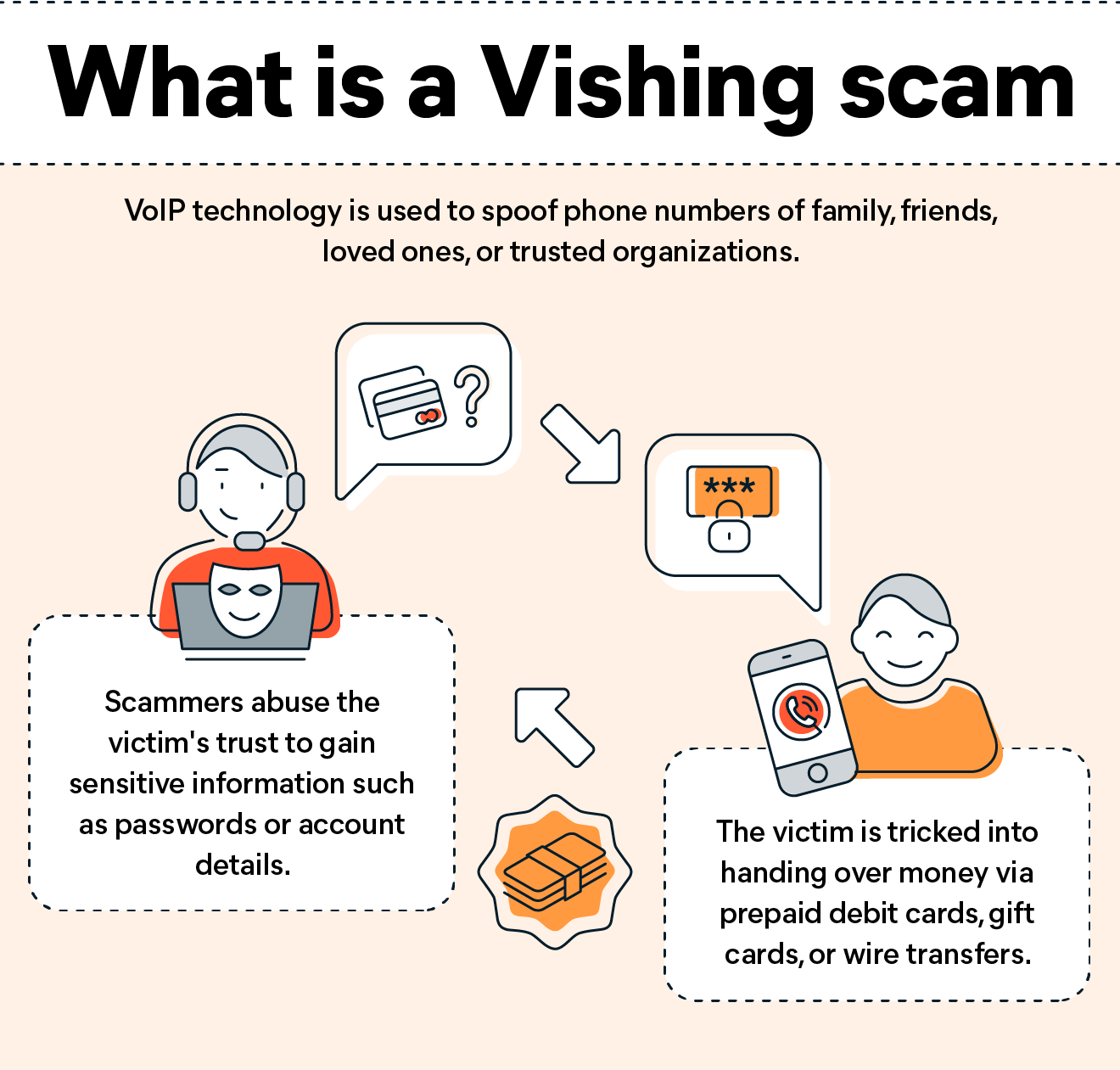
What is a Vishing scam, and how does it work?
The latest update to a decades-old scam, vishing involves using Voice Over Internet Protocol (VoIP) to fake phone numbers from family, friends, loved ones, businesses, government officials, banks, call center professionals, tech support, and more. By impersonating known individuals, scammers will try to have the victim share valuable information, buy prepaid debit cards, gift cards, or money orders, raise money for back taxes allegedly owed, or whatever means they can to access your data. As opposed to some types of cybercrime, vishing is used for both short-term and long-term fraud, making vishing a versatile tool in skilled hands.
Although many vishing scams take place over phone calls, the scam can also take advantage of direct messaging apps, emails, and text messages. In the case of phone calls, vishing can either feature robocalls or a live person calling you with a false pretense, either threatening or beneficial. Regardless of the method used, vishing relies on creating a false sense of panic or security in their intended victim as well as employing human factor techniques designed to create concerns for even the most skeptical user. Common human factor techniques include the classic Honey Trap of feigning sexual or romantic interest until gaining compromising data for extortion, a Diversion Theft where legitimate files are sent to spoofed email addresses, and the Watering Hole where a cybercriminal compromises a website the victim frequently visits to acquire their credentials.
History of Vishing Scams
Both vishing and its more well-known cousin phishing originated in the mid-1990s. Some of the earliest examples of phishing involved stealing America Online (AOL) user IDs and passwords. Although the basic technique of posing as a third party, such as a company employee, to verify personal and account data is still going strong, subsequent developments and improvements to VoIP technology have significantly raised the efficiency of vishing techniques. By taking advantage of technology to disguise their IP (Internet Protocol) and physical locations, as well as voice modulation software, vishers are particularly effective since pretending to verify data over the phone often leaves victims flustered and more easily manipulated.
Why are they becoming more of a threat now?
To quote from Avast’s recent article on vishing scams,
“Vishing scams have quickly become another major security threat for people around the globe. And although Interpol has cracked down in recent days, the risk of being targeted — and falling victim — to vishing scams has reached new heights.”
Interpol is becoming involved and has started to crack down.
Far from being isolated incidents or being constrained by geographic boundaries, vishing is an increasingly advanced form of social engineering that preys on human fears and instincts to separate victims from crucial personal and financial data. Due to the year-over-year increase in the overall number of victims and the staggering amount of money and data compromised, many national and international agencies are carrying out concerted efforts to push back against the rising tide. From March 8th to May 8th, 2022, Interpol carried out a massive two-month crackdown spanning almost 80 countries across the globe with the codename First Light 2022, demonstrating impressive levels of success. Notable statistics from the Interpol operation include:
- Almost 1,800 locations raided worldwide
- 3,000+ suspects identified
- Approximately 2,000 operators, fraudsters and money launderers arrested
- Approximately 4,000 bank accounts frozen
- Over USD 50 million of illicit funds seized
Those still wondering why an international crackdown on vishing has been carried out may be shocked to discover that some victims of vishing have been forced into illegal activities like faking their own kidnapping or sending photos of false injuries to elicit ransom payments. Other activities include using victims’ bank accounts to launder their own funds, a significant uptick in vishing scams with cybercriminals pretending to be bank officials, and even some as audacious vishers posing as Interpol agents themselves to exploit unwary people. Given all of that, Interpol deciding to take an interest in reigning in such activities begins to make much more sense.
What does a Vishing Scam look like?
By spoofing Caller ID and using auto-dialers to potentially contact hundreds of victims simultaneously, a scammer will often present themselves as an employee of your bank, credit union, website billing team, your boss, and so on.
One commonly used technique is contacting the victim on a pretense like verifying details of your account that should already be on record or claiming a sudden financial issue that needs to be rectified immediately. Other examples include receiving unsolicited messages about making a new investment or offering an unsolicited loan, posing as a member of the Social Security Administration or a Medicare biller, pretending to be someone from the IRS, and so on. They will often present themselves with a sense of urgency to prompt panic and rash behavior on your part, potentially threatening you with financial penalties and even the possibility of arrest and prosecution.
How can I protect myself from Vishing scams?
First and foremost, it is crucial to remain calm, consider the situation logically, and avoid making any decisions without first verifying the issue yourself. Another relatively simple technique is not opening any message or attachment sent from an unfamiliar party since this trick relies on our instinct to open attachments automatically without thinking first. It should also be noted that Social Security, Medicare, and the IRS would never reach out by text or email to confirm the information on file.
If you receive an automated call, do not respond to the prompts either verbally or with button presses, as you may be setting yourself up for future vishing attempts or providing them with a handy recording of your voice. Rather than calling back on the number provided by a suspicious message, you should take the time to research the company’s official phone number or email and contact them directly to verify.
For those seeking to avoid being vished, several simple strategies should help you avoid many vishing attacks. One of the easiest options is to register your phone number with the National Do Not Call Registry. Although this will not scare off determined criminals, it will reduce the overall level of traffic you have to deal with. Other solutions include letting strange calls go straight to voicemail for later review and simply terminating the call if you feel that you are at risk of being vished. You should also be wary of speaking with anyone who already possesses any amount of personal data and needs you to provide the remaining information.