Cloud is the technology that manages to connect different innovations and allow them to transform the market. We see cloud implementations everywhere, from parking lots to advanced financial software.
End users spend a lot on public cloud software, proving that the cloud is important for both personal and professional needs. However, the cloud is the foundation of the software-as-a-service (SaaS) business model.
With the amount of companies and individuals using SaaS applications and cloud storage, it’s obvious that there are going to be some risks. Malicious individuals have found ways to exploit numerous technologies, and the cloud isn’t an exception.
In this article, we’ll break down some of the key traits of cloud security, the most notorious risks that data security in the cloud faces, and some of the best practices for protecting SaaS applications.
Let’s dive in.
Cloud security explained
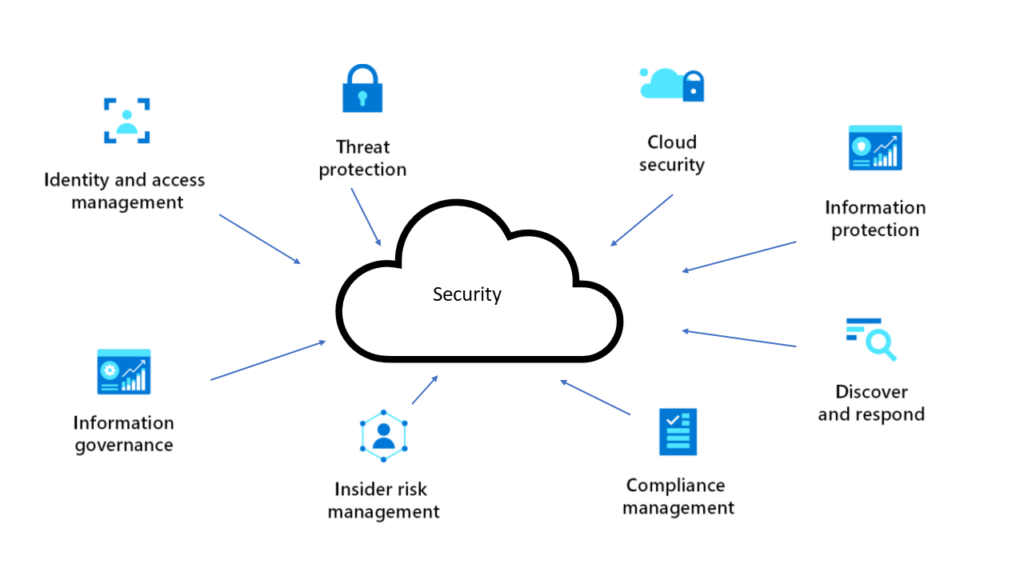
What’s interesting about cloud security is that it encompasses multiple cybersecurity disciplines. You’ll have to take care of data security in the cloud and other aspects, such as physical and network security.
The shared responsibility model is the basis for cloud security, meaning that both the cloud service provider (CSP) and its customers are responsible for ensuring cloud data security.
Cloud security is a broad set of policies, technologies, applications, and protocols that aim to protect the cloud. Common targets that need protection and are stored in the cloud include:
- Cloud computing infrastructure
- Virtualized IP
- Company data
- Applications
- Services
We have to give kudos to cloud security companies that offer their services without ever having an incident or significant downtime. These companies protect data extensively while ensuring compliance, business continuity, and protection against numerous risks and threats.
As a company developing a SaaS application, choosing a cloud security platform is essential for your operations and the protection of your customers.
Risks that cloud security faces
One of the largest risks that SaaS applications face occurs because of incompetent or careless personnel. Misconfigured security configuration, leaving default credentials, and inadequately implementing cybersecurity principles are significant vulnerabilities.
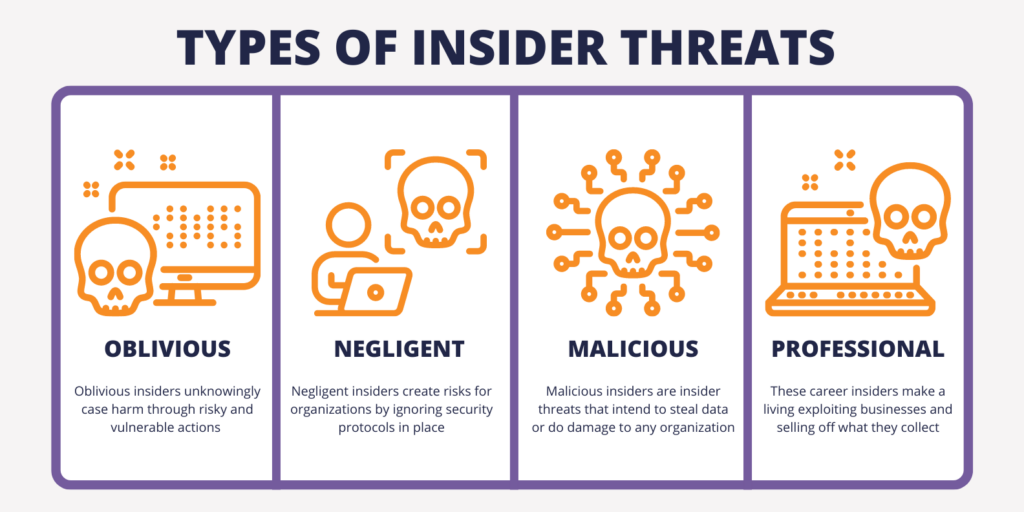
Internal risks include insider threats and inadequate monitoring. Insider risks are problematic because individuals within the company can cause intentional (or unintentional) harm.
Inadequate monitoring of traffic and incidents can make identifying malicious attacks and unauthorized access harder and more confusing in the long run.
However, it’s just as likely that hackers can attack your company as human error. They can use brute-force, denial of service, or XSS attacks to either harm your company’s systems or steal data.
Data breaches can lead to significant problems, mainly breaches of compliance regulations, which can then lead to fines and damage to your reputation.
However, failing to comply with compliance regulations can happen without external attacks. It can be a result of management negligence.
Compliance regulations need to be taken seriously. You should do what’s in your power to research the laws that apply to your company and follow them as guidelines.
Best practices for protecting SaaS applications
There are a variety of best practices to help improve your overall security and the security of your SaaS applications. However, we’ll cover some of the most common and helpful methods to reduce security threats.
Of course, with the recent rise of artificial intelligence, we’ll likely see numerous innovative solutions and new risks come about in the coming years.
1. Regular backups
One of the best pieces of advice anyone can give you about data is to do regular backups. This applies to both personal and professional lives. However, losing sentimental images won’t cause nearly as much damage as losing the data of thousands of users and/or employees.
Data needs to be protected — that’s non-negotiable. But if a risk unfolds unfavorably and you happen to become a victim of a data breach, backups can help you recover some or all of it. Some compliance regulations also require that you don’t lose data.
Backup costs vary depending on the cloud provider but the cost shouldn’t be prohibitive. Some cloud providers, like AWS, offer tiered storage options, allowing businesses to balance affordability and protection. AWS Backup pricing, for example, varies based on provisioned storage and Amazon RDS, among others.
By exploring these options and understanding their cost implications, businesses can choose a backup solution that safeguards their valuable SaaS data without exceeding their budget. This ensures both robust security and financial responsibility.
2. Physical security of data storage
Both physical threats and cyber ones endanger data security in the cloud. So, when choosing a cloud provider for your SaaS application, you should also consider where they are located and how they treat the physical security.
If someone physically steals or breaches the servers, you risk the loss or damage of sensitive data. This is one reason cloud storage offers greater security, especially for industries that handle a great deal of customer data.
Take, for instance, the hospitality industry. Hotel operations software generally stores guests’ data in the cloud and hotels implement specific security practices to ensure it’s protected. These measures include access controls and user permissions, performing regular security audits, as well as having disaster recovery and backup plans in place.
3. Protecting intellectual property
When protecting a SaaS application, you also need to consider that documents, meetings, and plans can pose security risks. Employees and other members of the meetings, for example, may need to sign non-disclosure agreements. This protects proprietary information and sets clear expectations for everyone involved.
Additionally, business directors and board members often handle sensitive data like financial reports and legal documents, so it’s essential for them to have a strong security system in place.
Utilizing board meeting software during meetings it’s a first step towards protecting all sensitive data. This type of software offers encryption of data, multi-factor authentication for user logins, and secure document sharing, and it’s compliant with data security regulations. This ensures that conversations and everything shared in the meeting remains private.
4. Strong access control
You can invest thousands of dollars into anti-viruses, firewalls, and cybersecurity, but inadequate access control can lead to security breaches regardless. Access control refers to the amount of privileges that individuals have.
In the context of an operating system, this explains whether they are allowed to change and execute files. However, when we’re talking about companies, access control can mean everything from accessing tools and resources to making changes in the infrastructure.
Access control needs to adhere to the least-privilege rule. This means no employee should have more privileges and access than they require.
For example, a writer should be able to access editorial guidelines. But there’s no reason why they should have access to the website’s backend.
5. Authentication measures
Poor authentication requirements are often not appropriately addressed, and this applies to both customers and employees.
To adequately secure your internal processes, you should ensure all employees use proper passwords and authentication measures. Strong and random passwords are essential protection against brute-force attacks and spidering.
On the other hand, multi-factor authentication can be helpful in preventing identity theft, stolen credentials, and brute-force attacks.
Password managers are also great pieces of software that can provide the necessary protection and help you meet password requirements.
6. Employee training
Even if you’re a software development company, you can’t expect all of your employees to have a deep understanding of cybersecurity.
Of course, your developers should be aware of secure coding methods and proper cloud environments, but a company also consists of marketers, writers, and other employees who aren’t as tech-savvy by default.
Training your employees to recognize and manage online risks can significantly improve your security. Employee training doesn’t have to be an advanced course. Rather, it should help them recognize some of the most common cyber threats along with practicing better access management.
Such training should teach them how to create strong passwords, notice phishing attempts, and what tools to use to protect themselves.
Training is crucial to preventing occasions where employees could download ransomware on their computers, which then leads to companies having to replace whole systems thanks to unauthorized access.
Employee training doesn’t only improve the security of your company. It also builds employee satisfaction and loyalty. These principles can be applied in their personal lives.
SaaS application security is crucial for ensuring success in the market
Many people who were unfortunately harmed by cyber threats believed that they were either safe or too unimportant to become a target. Not taking cloud security solutions seriously has been the cause of the downfall of numerous companies.
As an entrepreneur or developer working on a SaaS application, it’s essential to implement adequate security protocols to protect against internal and external threats.
Leveraging everything from the most basic methods, such as ensuring strict access control and a security policy, to innovative methods, such as third-party AI-powered cloud data protection software, can significantly improve your company’s security.
Even if your product is incredible and has numerous sales, a single security incident can harm your reputation in the long run and even cause you to go bankrupt. Investing in cloud platforms with the proper cybersecurity measures can prevent problems that can come with data breaches or the theft of intellectual property.
Take the time to research the proper private clouds (or hybrid clouds) for your SaaS. It’s never too late to invest in proper cloud data security. The last thing you want is a lack of visibility into your online protection. Take a proactive approach today!