CyberArk Review
 OUR SCORE 80%
OUR SCORE 80%
- What is CyberArk
- Product Quality Score
- Main Features
- List of Benefits
- Technical Specifications
- Available Integrations
- Customer Support
- Pricing Plans
- Other Popular Software Reviews
What is CyberArk ?
CyberArk is a security suite that helps to secure your devices, passwords and privileged accounts, among others. It consists of various security solutions and one of them, the Privileged Password Management and Control, aids organizations in meeting strict compliance and IT standards. This module helps you manage privileged passwords. Likewise, this software ensures you are always updated with compliance and audit policies and standards, so you avoid the risks of cyber threats and penalties. CyberArk boosts your processes in monitoring, securing and managing privileged accounts.Product Quality Score
CyberArk features
Main features of CyberArk are:
- Advanced Threat Protection
- Industrial Control Systems Security
- Windows Security
- IT Audit and Reporting
- DevOps Security
- Cloud & Virtualization Security
- Unix/Linux Security
- Confidential File Security
- Insider Threat Protection
- Remote Vendor Access Security
- Payment Card Industry Data Security Standard
CyberArk Benefits
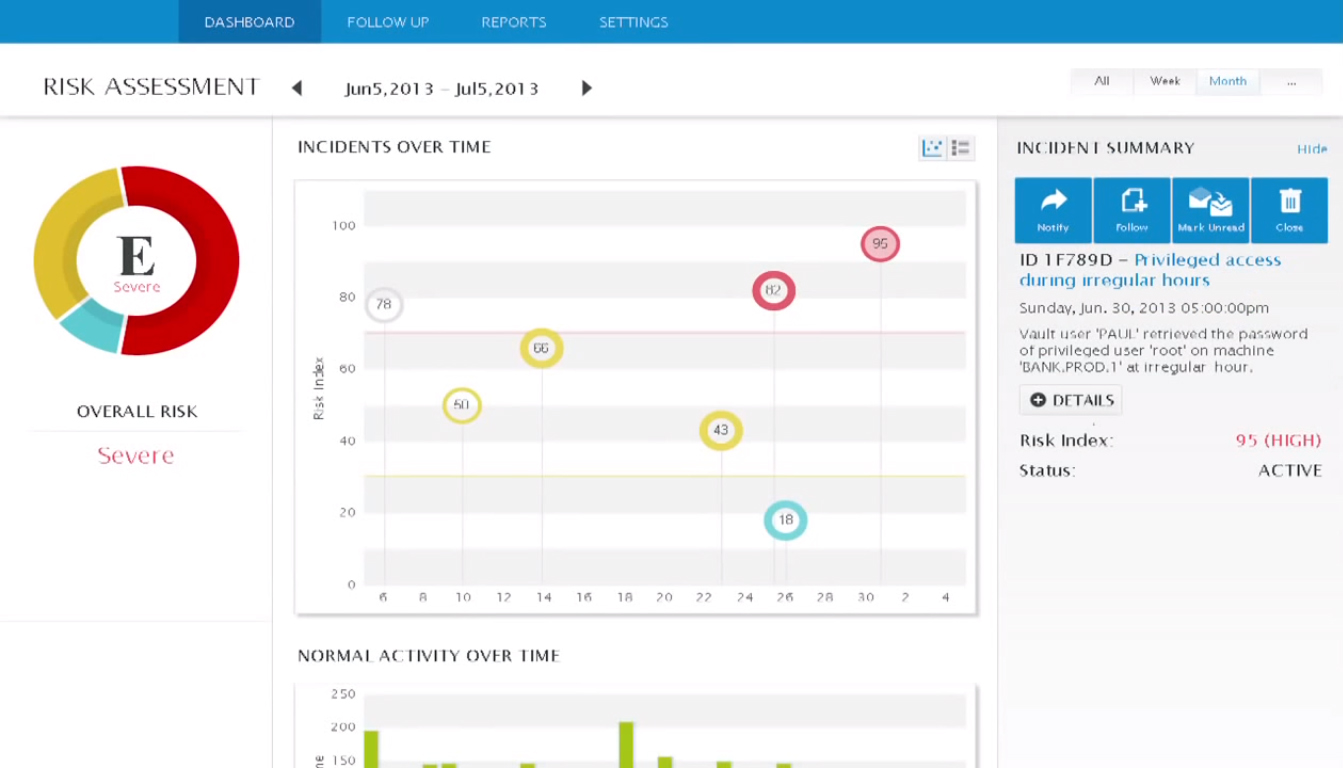
The main benefits of CyberArk are, it ensures compliance with regulations and I.T. standards, it protects your devices and passwords and it helps you streamline your security processes. Here are more details:
Automates various tasks
One way that CyberArk Privileged Password Management and Control manage to secure the passwords, networks, accounts, and devices is through automating the entire privileged lifecycle management processes. This results in an increased rate of workflow which in turn gives users more time to focus on pressing matters at hand.
Ensures accountability
The solution takes away the anonymity of the users that utilize the shared privileged accounts. Because of this, tracing the responsible party will be easier whenever something needs probing.
Flexible
The module is also versatile enough to provide the level of granularity and other protocols that audit requires. With this level of flexibility, enforcing the enterprise security policy that centers on privileged accounts is made easier. The needed changes for the requirements of audits are in line with the complexities of the passwords together with other factors.
Complete privilege control
Admins of the CyberArk Privileged Password Management and Control are given the power for the total control of access and capabilities of every privileged user. CyberArk gives the administrators the tools to define, modify and limit the access of certain privileged users. Access rights to users can be restricted to their “need to know” basis or it can also be granted depending on how the administrators decided on how it should be.
Generates secure and through audit reports
CyberArk has the capability to build and generate a highly detailed audit report on every single privileged accounts’ documents and access. Aside from that, every privileged activity can also be looked into. All these can be generated to be used for audit-proofing and for forensic analysis. Records’ integrity is kept since the data are all stored in a highly secured repository and one which cannot be tampered. The data repository is designed in a way that protects its contents from reconfiguration, unauthorized access and deletion of logs.
Technical Specifications
Devices Supported
- Web-based
- iOS
- Android
- Desktop
Customer types
- Small business
- Medium business
- Enterprise
Support Types
- Phone
- Online
CyberArk Integrations
The following CyberArk integrations are currently offered by the vendor:
The vendor didn’t provide any details on integration.
Video
Customer Support
Pricing Plans
CyberArk pricing is available in the following plans:





