Absolute Review
 OUR SCORE 84%
OUR SCORE 84%
- What is Absolute
- Product Quality Score
- Main Features
- List of Benefits
- Technical Specifications
- Available Integrations
- Customer Support
- Pricing Plans
- Other Popular Software Reviews
What is Absolute?
Absolute is a robust endpoint security software designed to help businesses in different industries to manage and secure all their endpoints. It is an innovative solution that redefines endpoint control and visibility, allowing businesses to protect endpoint users, data, devices, and applications. The platform provides actionable insights into how devices that are connected to their network access data and applications. Absolute includes powerful analytics and reporting tools that collect and analyze information about every device on a business network. This makes it easy for users to identify suspicious and anomalous activities, and counter them before they escalate. Besides, businesses can create strict security policies to automatically protect offline devices when unwarranted incidents happen.Product Quality Score
Absolute features
Main features of Absolute are:
- Remotely Recover Data
- Remotely Delete Sensitive Data
- Endpoint Investigations
- Risk Response
- Data Awareness
- Application Persistence Technology
- Reporting and Analytics
- Custom Query and Remediation
- Eliminate Dark Endpoints
Absolute Benefits
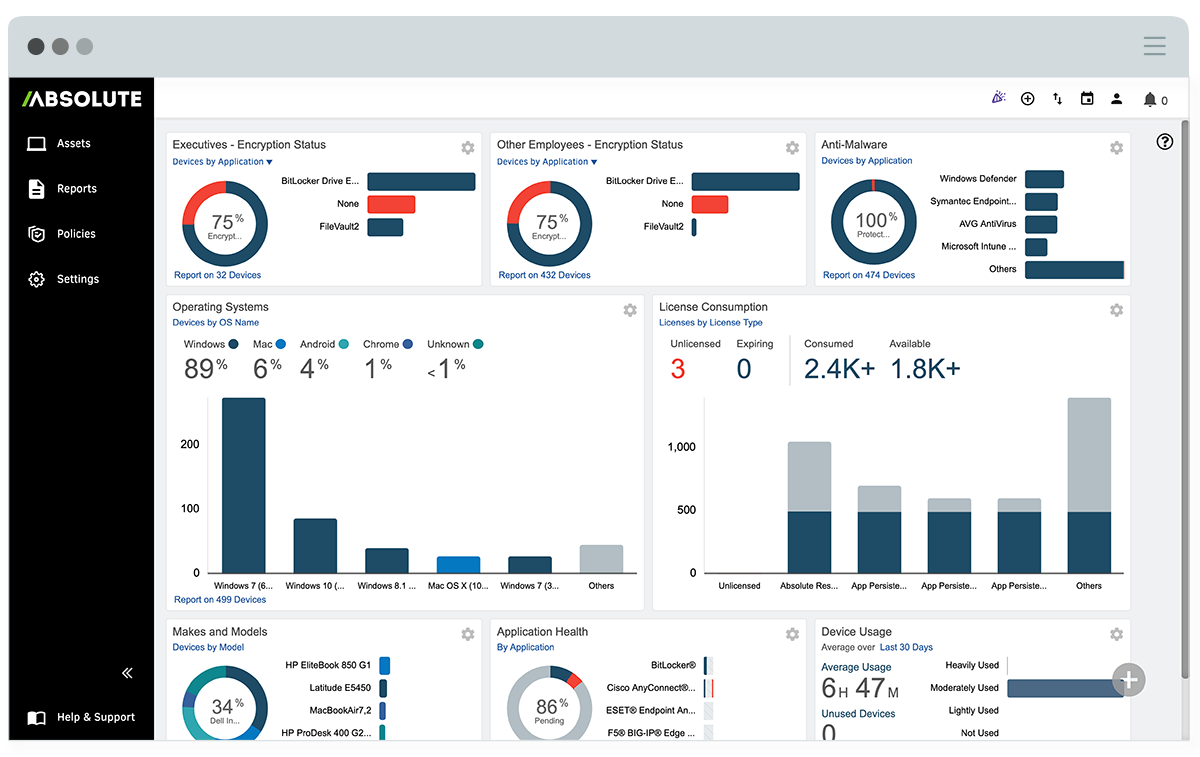
The main benefits of Absolute are its secure dark endpoints, self-healing technology, and protect sensitive business data. Here are more details:
Secure Dark Endpoints
Absolute is unique in that it enables businesses to secure all endpoints including those that are not seen by other systems. The platform secures endpoints such as off-the-network, lost, or stolen devices as well as devices that run without active security controls. By securing all endpoints, Absolute gives businesses, and IT professionals complete visibility and control over all applications, data, devices, and users who off or on their network.
Self-Healing Technology
Also, Absolute utilizes innovative, persistent technology that makes it easy to self-heal applications. The technology enables businesses to build complete application resiliency, prove compliance, and eliminate blind spots. With application persistence, businesses can easily enable self-healing encryption on all applications. This provides unprecedented visibility of every application regardless of where the hosting devices are.
Protect Sensitive Data
Better still, Absolute includes innovative data awareness features. These features allow users to pinpoint sensitive business data, locate where it is stored/hidden, and implement strict security controls to protect it. Also, users can quickly identify when a device or application that is not properly secured, holds at-risk business data. Consequently, users can easily remove such data from the unsecured devices and store them in a more secure location. Moreover, it’s easy to identify access and usage of data that bleaches compliance and security policies.
Technical Specifications
Devices Supported
- Web-based
- iOS
- Android
- Desktop
Customer types
- Small business
- Medium business
- Enterprise
Support Types
- Phone
- Online
Absolute Integrations
The following Absolute integrations are currently offered by the vendor:
No available information.
Video
Customer Support
Pricing Plans
Absolute pricing is available in the following plans:





